March/2021 Latest Braindump2go 350-401 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 350-401 Real Exam Questions!
QUESTION 367
Which two actions, when applied in the LAN network segment, will facilitate Layer 3 CAPWAP discovery for lightweight AP? (Choose two.)
A. Utilize DHCP option 17.
B. Configure WLC IP address on LAN switch.
C. Utilize DHCP option 43.
D. Configure an ip helper-address on the router interface
E. Enable port security on the switch port
Answer: CD
QUESTION 368
Refer to the exhibit. Which JSON syntax is derived from this data?

A. 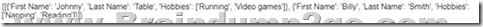
B. 
C. 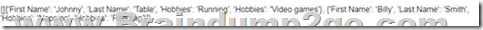
D. 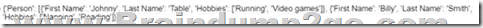
Answer: C
QUESTION 369
Which two network problems indicate a need to implement QoS in a campus network? (Choose two)
A. port flapping
B. excess jitter
C. misrouted network packets
D. duplicate IP addresses
E. bandwidth-related packet loss
Answer: BD
QUESTION 370
Which outcome is achieved with this Python code?

A. connects to a Cisco device using SSH nd exports the routing table information
B. displays the output of the show command in a formatted way
C. connects to a Cisco device using SSH and exports the BGP table for the prefix
D. connects to a Cisco device sing Telnet and exports the routing table information
Answer: C
QUESTION 371
—-QUESTION 3MISSING—–
A. DSW2(config if)#spanning-tree port-priority 128
B. DSW2(config-if)#spanning-tree port-priority 16
C. DSW2( onfig-if)#interface gi1/3
D. DSW1(config-if)#interface gi1/3
E. DWS1(config-if)#spanning-tree port-priority 0
Answer: DE
QUESTION 372
In a Cisco SD-Access solution, what is the role of the Identity Services Engine?
A. It is leveraged for dynamic endpoint to group mapping and policy definition.
B. It provides GUI management and abstraction via apps that share context.
C. it is used to analyze endpoint to app flows and monitor fabric status.
D. It manages the LISP EID database.
Answer: C
QUESTION 373
What is the data policy in a Cisco SD-WAN deployment?
A. list of ordered statements that define node configurations and authentication used within the SD-WAN overlay
B. Set of statements that defines how data is forwarded based on IP packet information and specific VPNs
C. detailed database mapping several kinds of addresses with their corresponding location
D. group of services tested to guarantee devices and links liveliness within the SD-WAN overlay
Answer: B
QUESTION 374
In a three-tier hierarchical campus network design, which action is a design best-practice for the core layer?
A. provide QoS prioritization services such as marking, queueing, and cl ssification for critical network traffic
B. provide redundant Layer 3 point-to-point links between the core devices for more predictable and faster convergence
C. provide advanced network security features such as 802. IX, DHCP snooping, VACLs, and port security
D. provide redundant aggregation for access layer devices and first-hop redundancy protocols such as VRRP
Answer: A
QUESTION 375
Refer to the exhibit. Which configuration change ensures that R1 is the active gateway whenever it is in a functional state for the 172.30.110.0724 network?
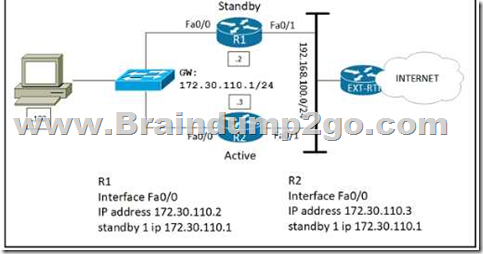
A. 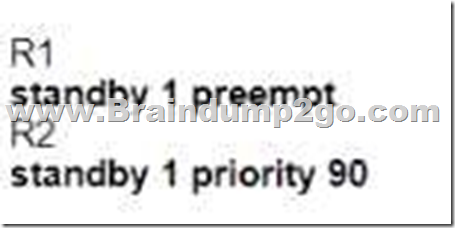
B. 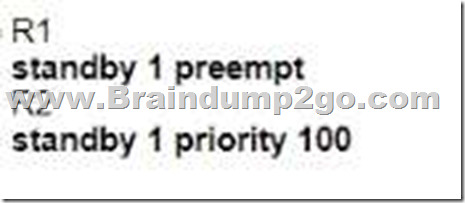
C. 
D. 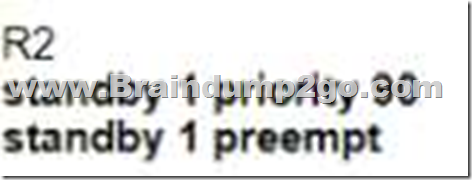
Answer: D
QUESTION 376
What ate two characteristics of Cisco SD-Access elements? (Choose two )
A. The border node is required for communication between fabric and nonfabric devices.
B. Fabric endpoints are connected directly to the border node
C. Traffic within the fabric always goes through the control plane node
D. The control plane node has the full RLOC-to-EID mapping database
E. The border node has the full RLOC-to-EID mapping database
Answer: AD
QUESTION 377
What is YANG used for?
A. scraping data via CLI
B. processing SNMP read-only polls
C. describing data models
D. providing a transport for network configuration data between client and server
Answer: C
QUESTION 378
Refer to the exhibit. Which action resolves the EtherChannel issue between SW2 and SW3?

A. Configure switchport mode trunk on SW2.
B. Configure switchport nonegotiate on SW3
C. Configure channel-group 1 mode desirable on both interfaces.
D. Configure channel-group 1 mode active on both interfaces.
Answer: D
QUESTION 379
A customer has completed the installation of a Wi-Fi 6 greenfield deployment at their new campus. They want to leverage Wi-Fi 6 enhanced speeds on the trusted employee WLAN. To configure the employee WLAN, which two Layer 2 security policies should be used? (Choose two.)
A. 802.1X
B. WPA (AES)
C. WPA2 (AES) jWEP
D. OPEN
Answer: AC
QUESTION 380
The following system log message is presented after a network administrator configures a GRE tunnel %TUN-RECURDOWN Interface Tunnel 0 temporarily disabled due to recursive routing. Why is Tunnel 0 disabled?
A. Because dynamic routing is not enabled
B. Because the tunnel cannot reach its tunnel destination
C. Because the best path to the tunnel destination is through the tunnel itself
D. Because the router cannot recursively identify its egress forwarding interface.
Answer: C
QUESTION 381
Which encryption hashing algorithm does NTP use for authentication?
A. SSL
B. MD5
C. AES128
D. AES256
Answer: B
QUESTION 382
Which data is properly formatted with JSON?
A. 
B. 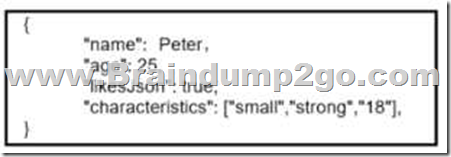
C. 
D. 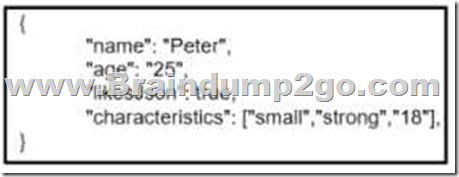
Answer: C
QUESTION 383
Refer to the exhibit. An engineer must assign an IP address of 192.168.1.1/24 to the GigabitEthemet1 in erface.
Which two commands must be added to the existing configuration to accomplish this task (Choose two)
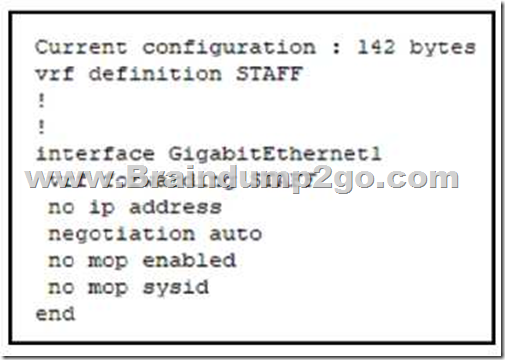
A. Router(config-vrf)# address-family ipv6
B. Router(config-if)# ip address 192.168.1.1 255.255.255.0
C. Router(config-vrf)# ip address 192.168.1.1 255.255.255.0
D. Router(config-if)# address-family ipv4
E. Router(config-vrf)# address-family ipv4
Answer: BE
QUESTION 384
How does Protocol Independent Multicast function?
A. In sparse mode it establishes neighbor adjacencies and sends hello messages at 5-second intervals.
B. It uses the multicast routing table to perform the multicast forwarding function.
C. It uses unicast routing information to perform the multicast forwarding function.
D. It uses broadcast routing information to perform the multicast forwarding function.
Answer: C
QUESTION 385
Which technology does VXLAN use to provide segmentation for Layer 2 and Layer 3 traffic?
A. bridge domain
B. VLAN
C. VRF
D. VNI
Answer: D
QUESTION 386
What are two methods of ensuring that the multicast RPF check passes without changing the unicast routing table? (Choose two.)
A. implementing static mroutes
B. disabling BGP routing protocol
C. implementing MBGP
D. disabling the interface of the router back to the multicast source
E. implementing OSPF routing protocol
Answer: AC
Explanation:
https://www.cisco.com/c/en/us/support/docs/ip/ip-multicast/16450-mcastguide0 html
QUESTION 387
Under which network conditions is an outbound QoS policy that is applied on a router WAN interface most beneficial?
A. under all network conditions
B. under network convergence conditions
C. under traffic classification and marking conditions
D. under interface saturation conditions
Answer: C
QUESTION 388
What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
A. real-time threat management to stop DDoS attacks to the core and access networks
B. real-time awareness of users, devices and traffic on the network
C. malware control
D. dynamic threat control for web traffic
Answer: A
QUESTION 389
A company has an existing Cisco 5520 HA cluster using SSO. An engineer deploys a new single Cisco Catalyst 9800 WLC to test new features. The engineer successfully configures a mobility tunnel between the 5520 cluster and 9800 WLC. Clients connected to the corporate WLAN roam seamlessly between access points on the 5520 and 9800 WLC. After a failure on the primary 5520 WLC, all WLAN services remain functional; however clients cannot roam between the 5520 and 9800 controllers without dropping their connection.
Which feature must be configured to remedy the issue?
A. mobility MAC on the 5520 cluster
B. mobility MAC on the 9800 WLC
C. new mobility on the 5520 cluster
D. new mobility on the 9800 WLC
Answer: B
QUESTION 390
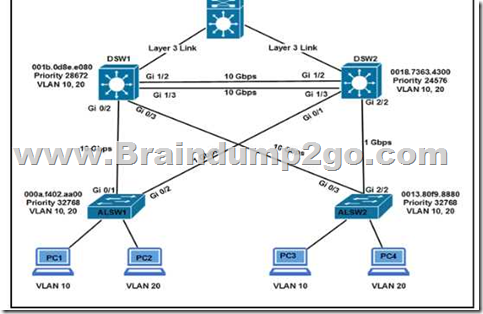
Refer to the exhibit. Assuming all links are functional, which path does PC1 take to reach DSW1?
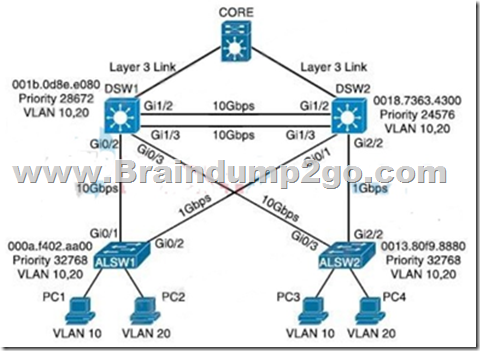
A. PC1 goes from ALSW1 to DSW1
B. PC1 goes form ALSW1 to DSW2 to ALSW2 to DSW1
C. PC1 goes from ALSW1 to DSW2 to Core to DSW1
D. PC1 goes from ALSW1 to DSW2 to DSW1
Answer: D
Explanation:
In the topology above, we see DSW2 has lowest priority 24576 so it is the root bridge for VLAN 10 so surely all traffic for this VLAN must go through it. All of DSW2 ports must be in forwarding state. And:
+ The direct link between DSW1 and ALSW1 is blocked by STP.
+ The direct link between DSW1 and ALSW2 is also blocked by STP.
Therefore PC1 must go via this path: PC1 -> ALSW1 -> DSW2 -> DSW1.
QUESTION 391
Drag and Drop Question
An engineer creates the configuration below. Drag and drop the authentication methods from the left into the order of priority on the right. Not all options are used.
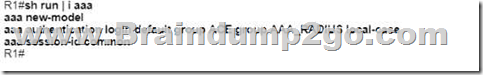
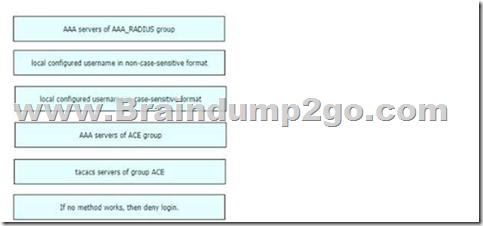
Answer:

Resources From:
1.2021 Latest Braindump2go 350-401 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-401.html
2.2021 Latest Braindump2go 350-401 PDF and 350-401 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1EIsykNTrKvqjDVs9JMySv052qbrCpe8V?usp=sharing
3.2021 Free Braindump2go 350-401 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/350-401-PDF-Dumps(367-391).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!
 |
 |
 |
 |
 |
|
|---|---|---|---|---|---|
 |
 |
 |
 |
 |
|
| Braindump2go | Testking | Pass4sure | Actualtests | Others | |
| $99.99 | $124.99 | $125.99 | $189 | $29.99/$49.99 | |
| Up-to-Dated | ✔ | ✖ | ✖ | ✖ | ✖ |
| Real Questions | ✔ | ✖ | ✖ | ✖ | ✖ |
| Error Correction | ✔ | ✖ | ✖ | ✖ | ✖ |
| Printable PDF | ✔ | ✖ | ✖ | ✖ | ✖ |
| Premium VCE | ✔ | ✖ | ✖ | ✖ | ✖ |
| VCE Simulator | ✔ | ✖ | ✖ | ✖ | ✖ |
| One Time Purchase | ✔ | ✖ | ✖ | ✖ | ✖ |
| Instant Download | ✔ | ✖ | ✖ | ✖ | ✖ |
| Unlimited Install | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Pass Guarantee | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Money Back | ✔ | ✖ | ✖ | ✖ | ✖ |