March/2022 Latest Braindump2go 350-701 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 350-701 Real Exam Questions!
QUESTION 368
Which configuration method provides the options to prevent physical and virtual endpoint devices that are in the same base EPG or uSeg from being able to communicate with each other with Vmware VDS or Microsoft vSwitch?
A. inter-EPG isolation
B. inter-VLAN security
C. intra-EPG isolation
D. placement in separate EPGs
Answer: B
QUESTION 369
Refer to the exhibit. What does the API key do while working with https://api.amp.cisco.com/v1/computers?
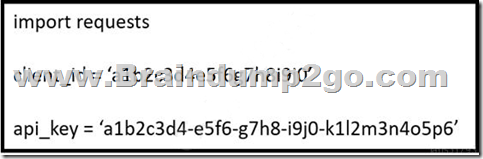
A. displays client ID
B. HTTP authorization
C. Imports requests
D. HTTP authentication
Answer: C
QUESTION 370
Which statement describes a serverless application?
A. The application delivery controller in front of the server farm designates on which server the application runs each time.
B. The application runs from an ephemeral, event-triggered, and stateless container that is fully managed by a cloud provider.
C. The application is installed on network equipment and not on physical servers.
D. The application runs from a containerized environment that is managed by Kubernetes or Docker Swarm.
Answer: B
QUESTION 371
Which baseline form of telemetry is recommended for network infrastructure devices?
A. SDNS
B. NetFlow
C. passive taps
D. SNMP
Answer: D
QUESTION 372
In which scenario is endpoint-based security the solution?
A. inspecting encrypted traffic
B. device profiling and authorization
C. performing signature-based application control
D. inspecting a password-protected archive
Answer: C
QUESTION 373
Refer to the exhibit. What is the result of the Python script?
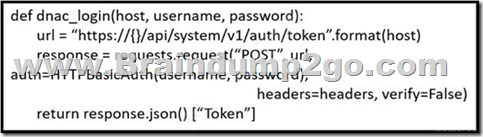
A. It uses the POST HTTP method to obtain a username and password to be used for authentication.
B. It uses the POST HTTP method to obtain a token to be used for authentication.
C. It uses the GET HTTP method to obtain a token to be used for authentication.
D. It uses the GET HTTP method to obtain a username and password to be used for authentication
Answer: B
QUESTION 374
Why is it important to patch endpoints consistently?
A. Patching reduces the attack surface of the infrastructure.
B. Patching helps to mitigate vulnerabilities.
C. Patching is required per the vendor contract.
D. Patching allows for creating a honeypot.
Answer: B
QUESTION 375
An engineer enabled SSL decryption for Cisco Umbrella intelligent proxy and needs to ensure that traffic is inspected without alerting end-users. Which action accomplishes this goal?
A. Restrict access to only websites with trusted third-party signed certificates.
B. Modify the user’s browser settings to suppress errors from Cisco Umbrella.
C. Upload the organization root CA to Cisco Umbrella.
D. Install the Cisco Umbrella root CA onto the user’s device.
Answer: D
QUESTION 376
What is the purpose of joining Cisco WSAs to an appliance group?
A. All WSAs in the group can view file analysis results.
B. The group supports improved redundancy
C. It supports cluster operations to expedite the malware analysis process.
D. It simplifies the task of patching multiple appliances.
Answer: B
QUESTION 377
Why should organizations migrate to an MFA strategy for authentication?
A. Single methods of authentication can be compromised more easily than MFA.
B. Biometrics authentication leads to the need for MFA due to its ability to be hacked easily.
C. MFA methods of authentication are never compromised.
D. MFA does not require any piece of evidence for an authentication mechanism.
Answer: A
QUESTION 378
Which technology should be used to help prevent an attacker from stealing usernames and passwords of users within an organization?
A. RADIUS-based REAP
B. fingerprinting
C. Dynamic ARP Inspection
D. multifactor authentication
Answer: A
QUESTION 379
Which type of attack is MFA an effective deterrent for?
A. ping of death
B. phishing
C. teardrop
D. syn flood
Answer: B
QUESTION 380
Which Cisco cloud security software centrally manages policies on multiple platforms such as Cisco ASA, Cisco Firepower, Cisco Meraki, and AWS?
A. Cisco Defense Orchestrator
B. Cisco Configuration Professional
C. Cisco Secureworks
D. Cisco DNAC
Answer: A
QUESTION 381
Which Cisco security solution determines if an endpoint has the latest OS updates and patches installed on the system?
A. Cisco Endpoint Security Analytics
B. Cisco AMP for Endpoints
C. Endpoint Compliance Scanner
D. Security Posture Assessment Service
Answer: D
QUESTION 382
Using Cisco Cognitive Threat Analytics, which platform automatically blocks risky sites, and test unknown sites for hidden advanced threats before allowing users to click them?
A. Cisco Identity Services Engine
B. Cisco Enterprise Security Appliance
C. Cisco Web Security Appliance
D. Cisco Advanced Stealthwatch Appliance
Answer: C
QUESTION 383
What are two things to consider when using PAC files with the Cisco WSA? (Choose two.)
A. If the WSA host port is changed, the default port redirects web traffic to the correct port automatically.
B. PAC files use if-else statements to determine whether to use a proxy or a direct connection for traffic between the PC and the host.
C. The WSA hosts PAC files on port 9001 by default.
D. The WSA hosts PAC files on port 6001 by default.
E. By default, they direct traffic through a proxy when the PC and the host are on the same subnet.
Answer: BC
QUESTION 384
What is a description of microsegmentation?
A. Environments deploy a container orchestration platform, such as Kubernetes, to manage the application delivery.
B. Environments apply a zero-trust model and specify how applications on different servers or containers can communicate.
C. Environments deploy centrally managed host-based firewall rules on each server or container.
D. Environments implement private VLAN segmentation to group servers with similar applications.
Answer: B
QUESTION 385
Which Cisco WSA feature supports access control using URL categories?
A. transparent user identification
B. SOCKS proxy services
C. web usage controls
D. user session restrictions
Answer: A
QUESTION 386
Which technology limits communication between nodes on the same network segment to individual applications?
A. serverless infrastructure
B. microsegmentation
C. SaaS deployment
D. machine-to-machine firewalling
Answer: B
QUESTION 387
Which IETF attribute is supported for the RADIUS CoA feature?
A. 24 State
B. 30 Calling-Station-ID
C. 42 Acct-Session-ID
D. 81 Message-Authenticator
Answer: A
Resources From:
1.2022 Latest Braindump2go 350-701 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-701.html
2.2022 Latest Braindump2go 350-701 PDF and 350-701 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1Fz2rtzfDdCvomlIPqv3RZzNAkMIepErv?usp=sharing
3.2021 Free Braindump2go 350-701 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/350-701-PDF-Dumps(368-387).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!
 |
 |
 |
 |
 |
|
|---|---|---|---|---|---|
 |
 |
 |
 |
 |
|
| Braindump2go | Testking | Pass4sure | Actualtests | Others | |
| $99.99 | $124.99 | $125.99 | $189 | $29.99/$49.99 | |
| Up-to-Dated | ✔ | ✖ | ✖ | ✖ | ✖ |
| Real Questions | ✔ | ✖ | ✖ | ✖ | ✖ |
| Error Correction | ✔ | ✖ | ✖ | ✖ | ✖ |
| Printable PDF | ✔ | ✖ | ✖ | ✖ | ✖ |
| Premium VCE | ✔ | ✖ | ✖ | ✖ | ✖ |
| VCE Simulator | ✔ | ✖ | ✖ | ✖ | ✖ |
| One Time Purchase | ✔ | ✖ | ✖ | ✖ | ✖ |
| Instant Download | ✔ | ✖ | ✖ | ✖ | ✖ |
| Unlimited Install | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Pass Guarantee | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Money Back | ✔ | ✖ | ✖ | ✖ | ✖ |